our data and security commitments to our customers
Committed to Customer Data Protection
We know that your company, client, and case information is highly sensitive and confidential. That’s why protecting your data is our top priority. Our expert team constantly updates and rigorously tests our network and applications to ensure they remain secure. Team members also undergo regular security training and obtain industry security certifications. In an independent audit, our systems were certified as compliant for their ability to protect against the latest security threats and breaches.

secure data management & privacy protection
Certified SOC 2 Type II Compliant
As part of our ongoing security efforts, we are compliant with the voluntary SOC 2 Type II framework. It’s a set of standards created by the American Institute of CPAs (AICPA) to evaluate how well companies manage and protect consumer data. SOC 2 Type II compliance is a recognized standard for managing customer data, particularly among technology and cloud-based companies.
Five Trust Service Criteria
The SOC 2 Type II is built on five Trust Services Criteria (TSC), which are the guiding principles used to evaluate how companies handle customer data. The audit evaluates how closely internal systems and controls align with the framework.
Security
Assessing whether systems are protected against unauthorized access
Availability
Ensuring systems and data are readily available according to SLAs and contract terms
Processing Integrity
Whether data is processed accurately, completely, and in a timely manner
Confidentiality
Whether sensitive business information is protected from unauthorized disclosure
Privacy
Ensures personal information is properly collected, used, retained, disclosed, or disposed of
SSL Certificates
All traffic is secured using TLS protocols, ensuring that data transmitted between your browser and our servers remains private and is protected from interception. Certificates are renewed automatically and monitored continuously, so connections are never left vulnerable to expiration or misconfiguration.
Top Firewall Solutions
We protect our infrastructure with enterprise-grade firewalls that monitor and filter all network traffic in real time. Our systems block unauthorized access attempts, mitigate application-layer attacks such as SQL injection or cross-site scripting, and automatically detect malicious bots. These defenses ensure that only legitimate, secure traffic reaches our network.
Database & Server Backups
We protect critical data with routine, automated backups across databases and servers. Backups are encrypted, distributed, and stored in secure locations to ensure resilience against hardware failures, corruption, or data loss. Restoration processes are tested regularly, guaranteeing that client systems can be recovered quickly and reliably if needed.
Secure Data Storage
We protect all client data with industry-standard AES-256 encryption. Stored information is distributed and backed up across secure locations, ensuring both confidentiality and availability. Continuous monitoring and access controls prevent unauthorized access, keeping your data secure, accessible, and reliable at all times.
Ready to Get Started?
When you go with our services, you can rest assured that your client data—and your clients—are always safe with us. Contact us today to get started.
WHAT WE DO
Other Solutions
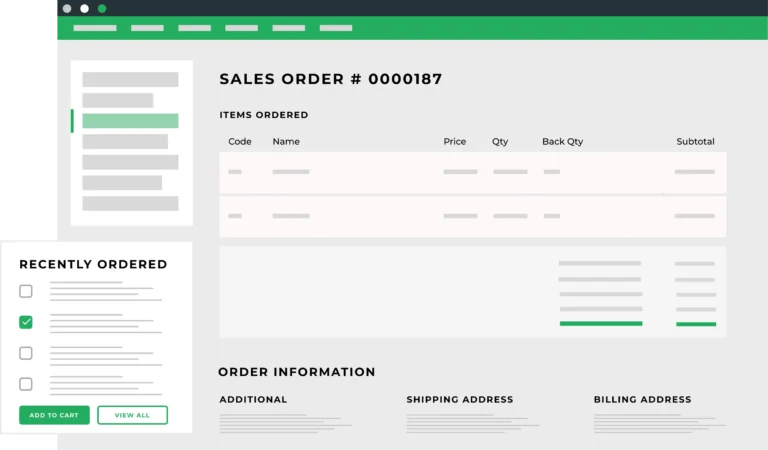
E-Link
E-Link forms a seamless, highly customizable bi-directional data synch between Sage and Magento Adobe Commerce, Shopify, and WooCommerce.
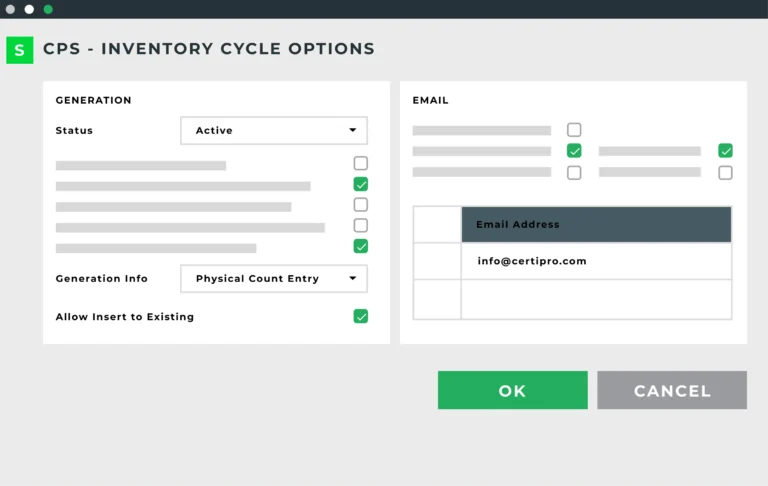
Automated Inventory Cycle Count
AICC automates the cycle counting process in Sage 100, Sage 300, and Sage 500, including automatically determining what items should be counted each day.